Random thoughts: goals and company types in tech world
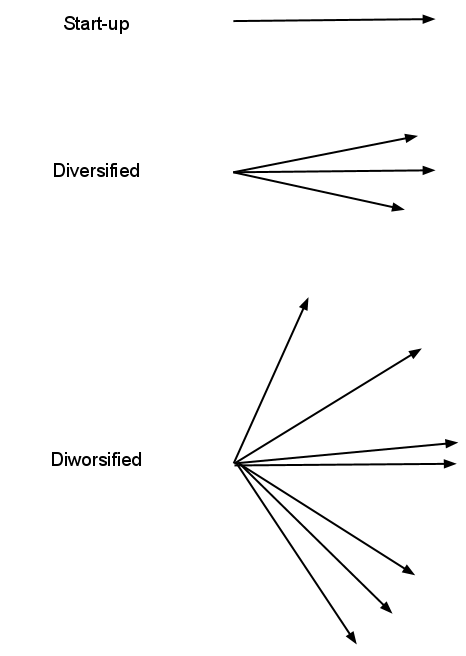
Start-up One goal May have multiple products but all products are aimed at a single goal. All teams are working towards the same goal. Diversified Multiple similar goals Have several products (or several parts of a single product) aimed towards different goals. Teams gain by helping each other. The goals to some extent are complementary but (naturally with time) diverge away from each other. The tipping point comes when the goals become orthogonal and thus, any bonding between teams working on (orthogonal) goals goes to zero. ...

